This weekend I started setting up the core of the provider network. This mainly consisted of configuring MPLS and MP-BGP to run L3VPNs between provider nodes. I also setup a secondary internet connection, which will primarily be used to run active-active tunnels from sites into the MPLS core.
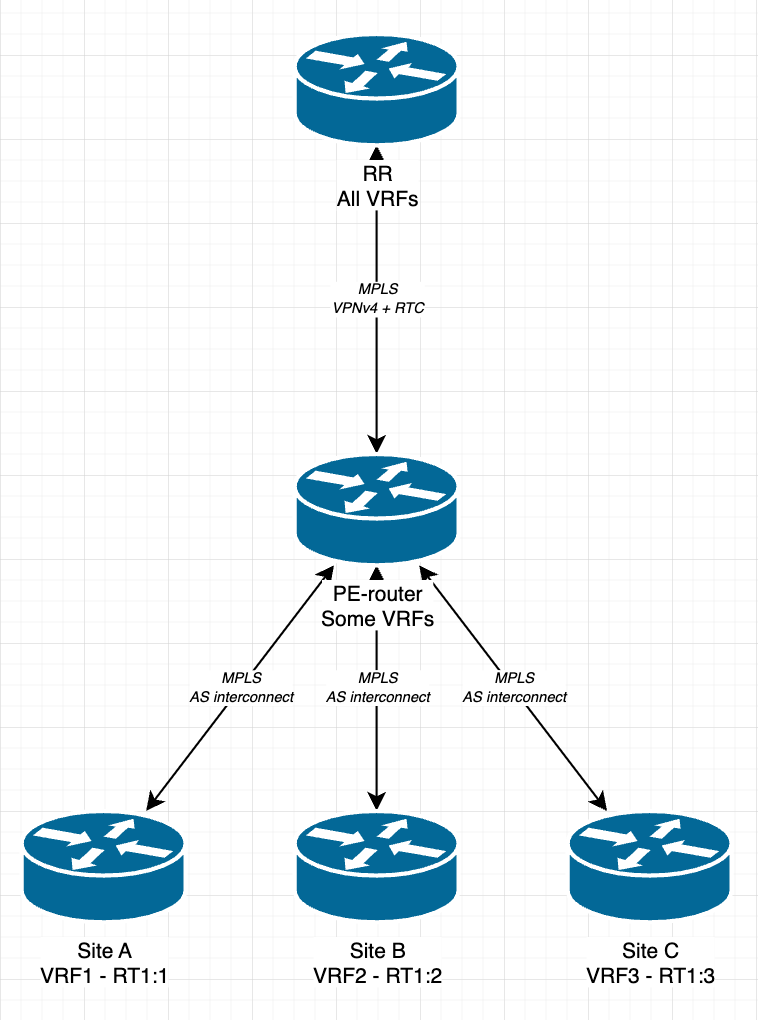
One big goal of this new setup is to allow access from a site to any allowed VRF in the provider network. Each site is to have their own VRF, which automatically allows access from the provider core into all networks for a given customer. Like I mentioned in the initial post for this project, this will be done through MPLS over DMVPN. I hope to be able to setup the first connection from my home site into the provider core this or next week. This would allow me to multiplex all the VRF:s and access them on L3 from home.
The MP-BGP peering is done between loopback addresses on each node. To propagate the loopback addresses dynamically within the network OSPF will be used. The main reason to run OSPF over ISIS is that ISIS is an L2 protocol, which limits the ability to build underlay peering over virtual interfaces. Since I want to run the OSPF peering out to the sites it is essential that we are able to use different tunneling/encapsulation methods for spanning the network across the WAN, the capabilities of OSPF will be essential. The idea is to run each site as it’s own area, in order to minimize the reconverge time particularly in the provider core.
Preferably I would like to run each site as a different AS, since each site will be treated as a customer to the provider. But this I have not yet decided. This would then entail that I would need to setup MPLS interconnects between the different AS, which is not something I have done yet. :S
I also would like to find a way of filtering which route-targets are allowed to be exported to each peer, since not all sites will be managed by me. I have already set up route-target constraint in the provider core, which allows the RR and each P/PE router to negotiate which VPN routes they should send to each other. This is preferred if you have really large routing tables, since the default behavior is to just send all route-targets and then let the receiving end drop the route-targets which it does not want. I will have to continue researching this matter, but if anyone has any tips, then please leave a comment below.
Leave a Reply